.png)

The cloud services market is expanding quickly, with projections reaching $30.4 billion by 2029. With this growth, more businesses are shifting their workloads to cloud platforms. Along with this shift comes the responsibility to secure applications, data, and infrastructure from cyber threats.
Cloud security architecture provides the structure needed to protect these cloud-based systems. It includes defined layers, tools, and strategies that work together to reduce risk, protect customer data, and meet regulatory standards.
This guide explains how cloud security architecture functions, why it is essential in modern cloud environments, and how to implement it effectively. You’ll also explore tools commonly used by security teams and methods to protect against phishing, ransomware, and misconfiguration-related threats.
TL;DR - Key Takeaways
Here’s a brief overview before diving deeper into the details:
Cloud security architecture is a detailed blueprint that defines how cloud platforms are protected. It includes a layered approach where identity controls, encryption methods, network design, and monitoring tools work together to keep your system safe.
Instead of simply adding security after deployment, this approach starts from the beginning. Similar to designing a building with entry controls, security zones, and monitoring systems, cloud security also requires thoughtful planning.
To understand its full impact, let’s examine why this architecture is critical today.
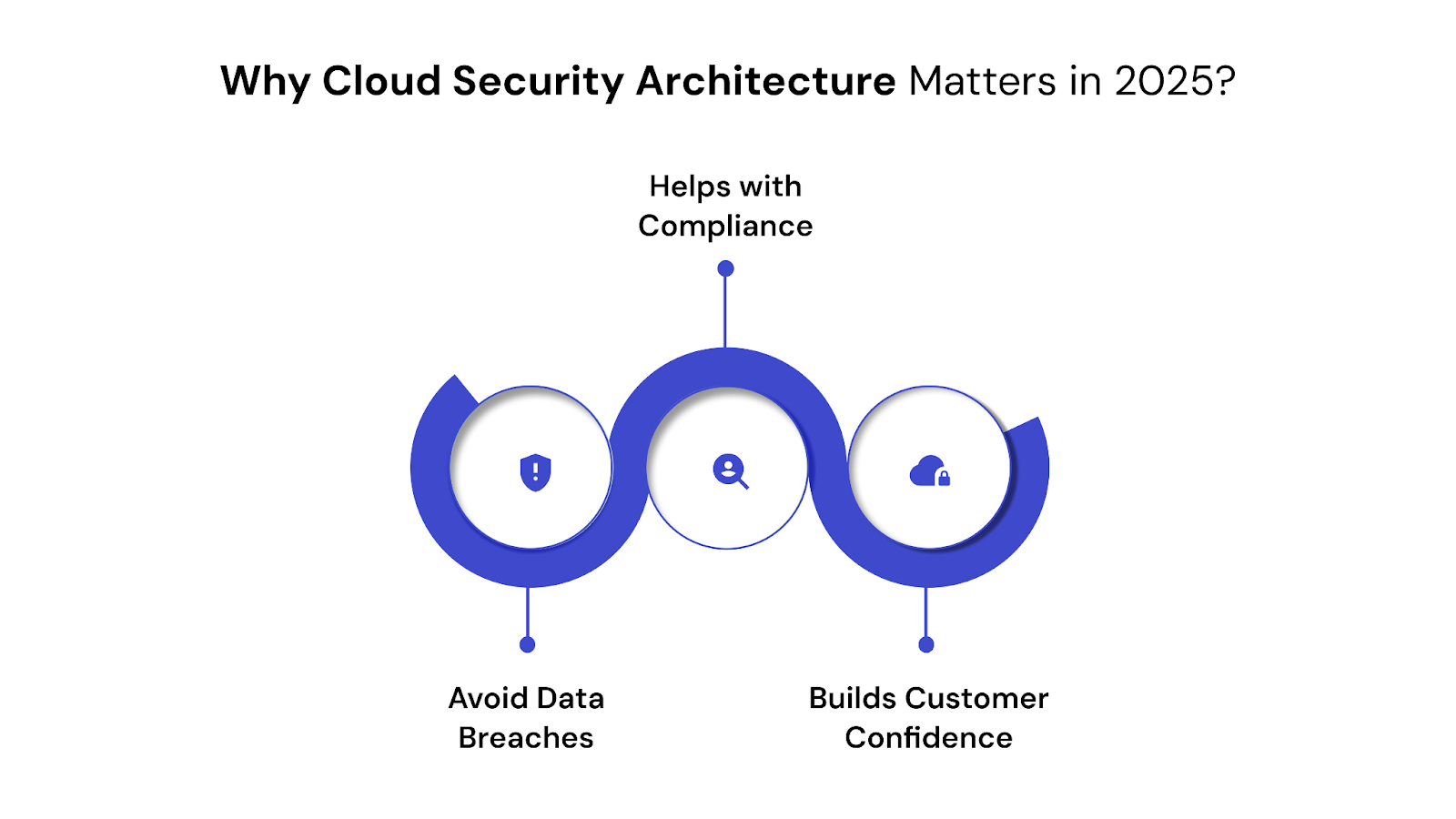
The importance of cloud security continues to rise in response to the growing number of cloud threats. According to the IBM Cost of a Data Breach Report 2024, misconfigured cloud services accounted for 10% increase of all breaches globally. In India, the average cost of a breach crossed 195 million.
Cloud systems need a security-first design for the following reasons:
1. Prevents Costly Data Breaches
Misconfigured storage, weak access policies, or unencrypted data can result in major data leaks. A security architecture helps close these gaps early and reduces the chances of financial or reputational loss.
2. Helps with Compliance
Industries such as finance, healthcare, and e-commerce must comply with standards like GDPR, PCI DSS, and HIPAA. A well-structured architecture simplifies compliance checks and reduces the effort needed for audits.
3. Builds Customer Confidence
A secure cloud infrastructure builds trust. In a 2024 PwC survey, 82 percent of Indian consumers said they are unlikely to engage with companies that have experienced a recent data breach. Strengthening your cloud security shows that you take responsibility for protecting customer data.
Also read: What is Cloud Governance: Frameworks, Models, and Challenges
Let’s now explore the types of security architectures and how they operate across cloud platforms.
Cloud security architectures define how protection is structured across different platforms and services. They combine tools, policies, and service models to safeguard data, control access, and monitor threats across environments.
These architectures support a variety of cloud models including public, hybrid, and multi-cloud. Each setup uses provider-specific tools and follows shared responsibility principles to balance security between the provider and customer.
The table below highlights key types and their focus areas:
Each model contributes to a layered defense system that scales with your infrastructure. Together, they help reduce exposure to risks while aligning with compliance needs.
Next, we’ll look at the building blocks that make up a strong cloud security architecture.
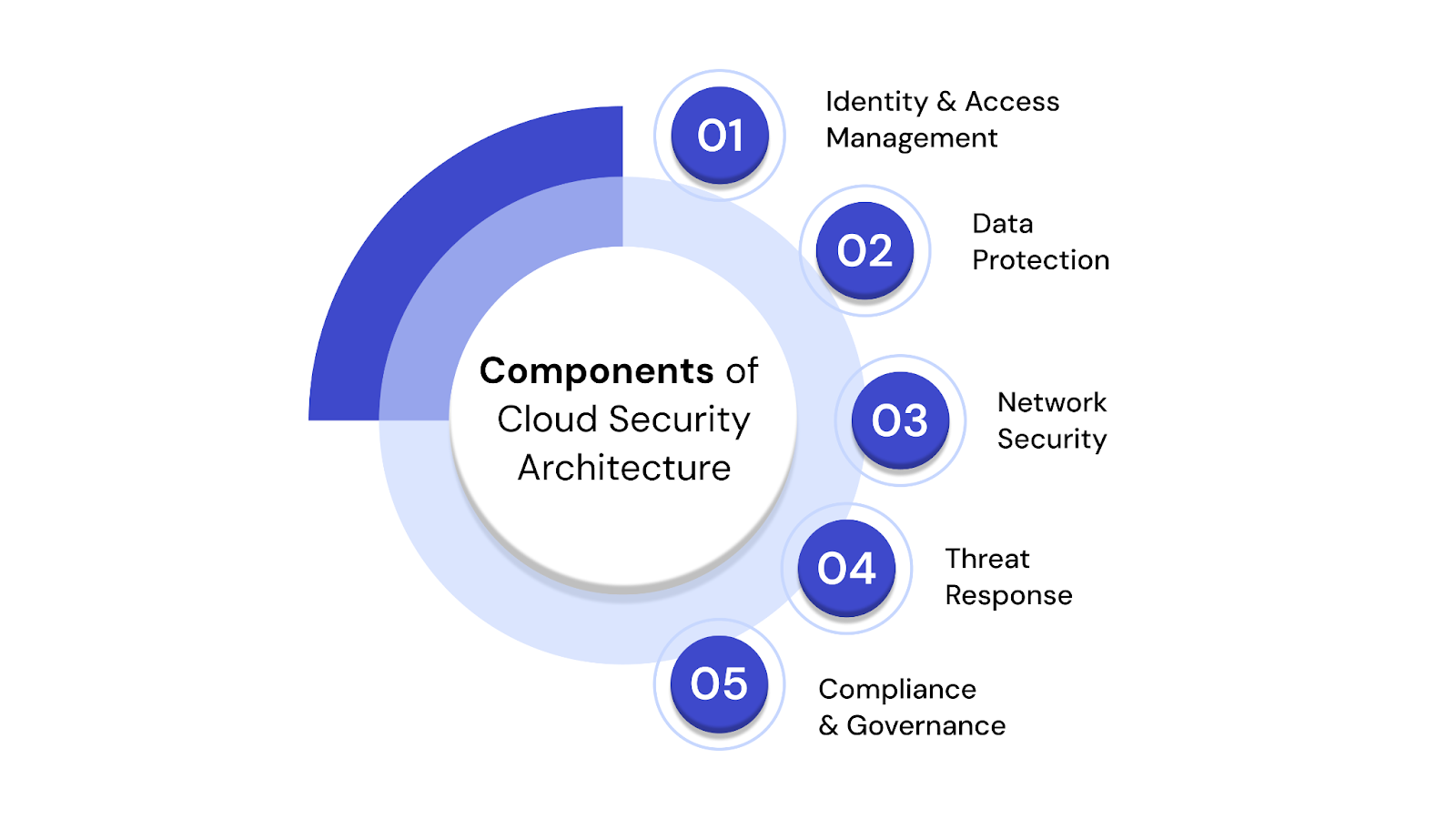
Cloud security architecture is not a single tool or product. It is a layered system built to protect cloud-based assets, applications, and users across environments. Each layer addresses a specific aspect of security, and together, they form a complete framework that supports operational efficiency while reducing risk.
The components listed below represent the core pillars of this architecture. Each plays a specific role in ensuring a secure and compliant cloud infrastructure.
IAM focuses on defining who can access your cloud systems and what actions they are allowed to perform. It helps ensure that users only interact with the resources they genuinely need, which reduces the risk of insider misuse or external threats.
Key practices used in IAM include:
Data protection ensures that sensitive information is secure during storage, processing, and transmission. This component focuses on encryption, cloud optimization strategies and real-time policies that minimize data loss or exposure.
Common approaches include:
Network security manages the safe flow of data within cloud environments. It aims to restrict unauthorized access, prevent attacks, and ensure that communications remain secure.
Tools and principles commonly used:
Detecting potential threats early and responding quickly is critical for minimizing impact. This layer includes tools that monitor for suspicious activity and take automatic or manual actions in response.
Technologies used in this area:
Governance ensures that your cloud environment meets industry regulations and aligns with internal security policies. It also clarifies which party is responsible for which areas of the system.
Key elements include:
For businesses adopting cloud platforms, building a strong security architecture is essential for protecting critical systems and ensuring compliance. Learn more about cloud migration strategies here.
Let’s move forward and look at the core principles that drive effective cloud security.
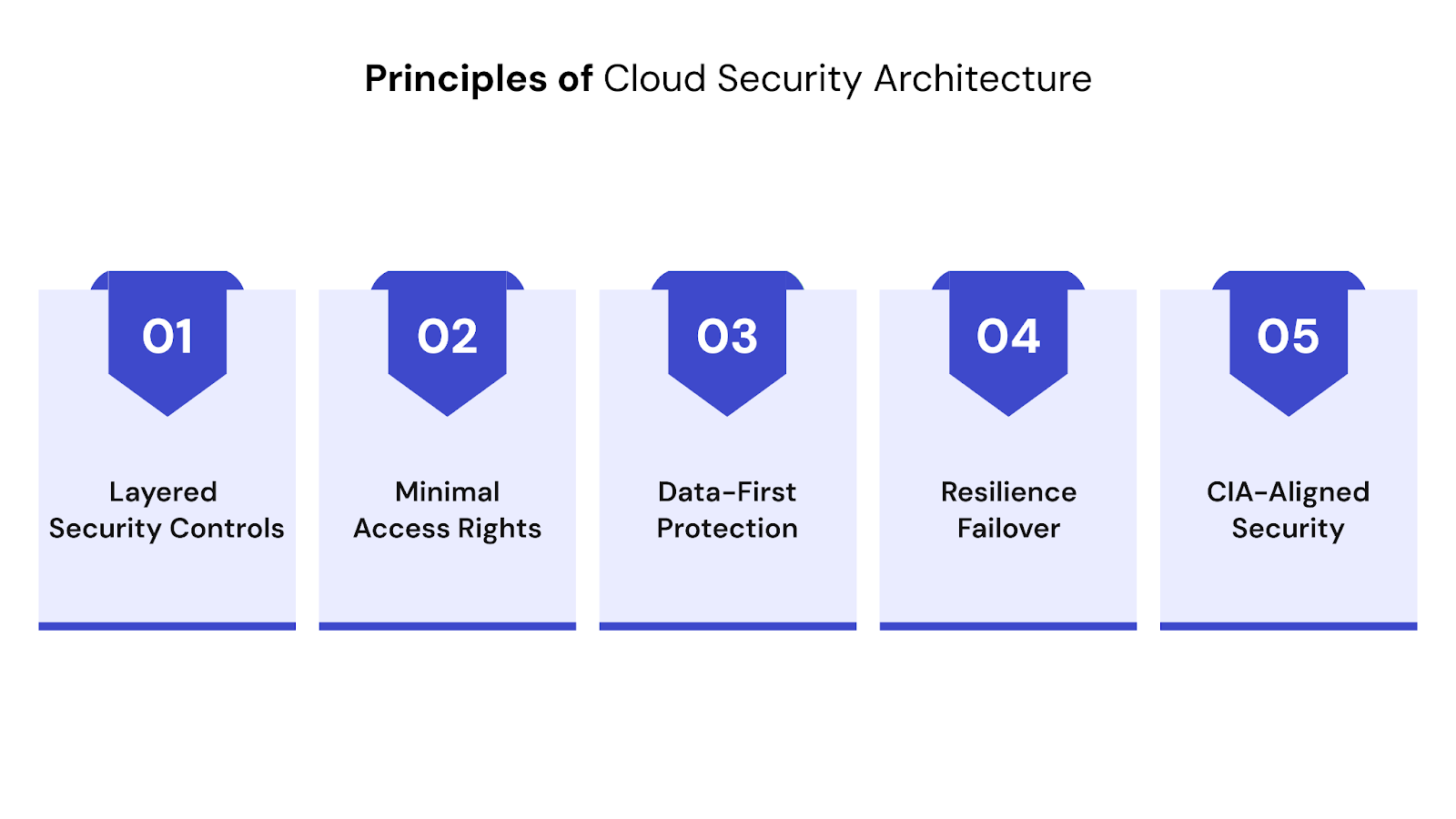
A secure cloud system isn’t built with a single layer of protection. Instead, it relies on multiple well-planned principles that work together to prevent breaches, limit damage, and maintain system availability. These foundational ideas apply across cloud platforms like AWS, Azure, Google Cloud, and hybrid environments.
Below are five widely accepted principles that help ensure a resilient and secure cloud setup.
Cloud systems require multiple safeguards working across all levels from user access to infrastructure. Relying on one barrier is never enough. Each layer should slow down, detect, or block potential attacks.
This approach helps minimize risk by ensuring that if one control fails, others are in place to protect the environment.
Implementation examples:
Granting only the permissions needed to perform a task limits how much damage a compromised account or service can cause. This principle, known as least privilege, reduces the chance of internal misuse or accidental exposure.
Systems should be audited regularly to keep access levels aligned with current roles.
Implementation examples:
Rather than focusing only on the network or perimeter, this principle places cloud data security directly around the data. The goal is to make sure sensitive information remains protected, regardless of where it is stored or how it moves.
This approach becomes critical in environments where data flows between services, regions, or even providers.
Implementation examples:
System downtime or data loss during an attack can be just as damaging as a breach. That’s why cloud security design must include redundancy, backups, and tested recovery plans.
By planning for outages and disruptions, you can reduce the impact of unexpected failures.
Implementation examples:
The Confidentiality, Integrity, and Availability (CIA) triad guides most security planning. These three goals ensure that your data is safe, accurate, and accessible only to the right people.
Each element helps define how to secure different parts of your cloud system.
Implementation examples:
With the growing need to protect data across complex cloud environments, understanding key security risks and solutions becomes essential. Explore our detailed guide on cloud data security here.
Understanding how to apply these principles in real setups is the next step. That’s where building your own architecture comes in.
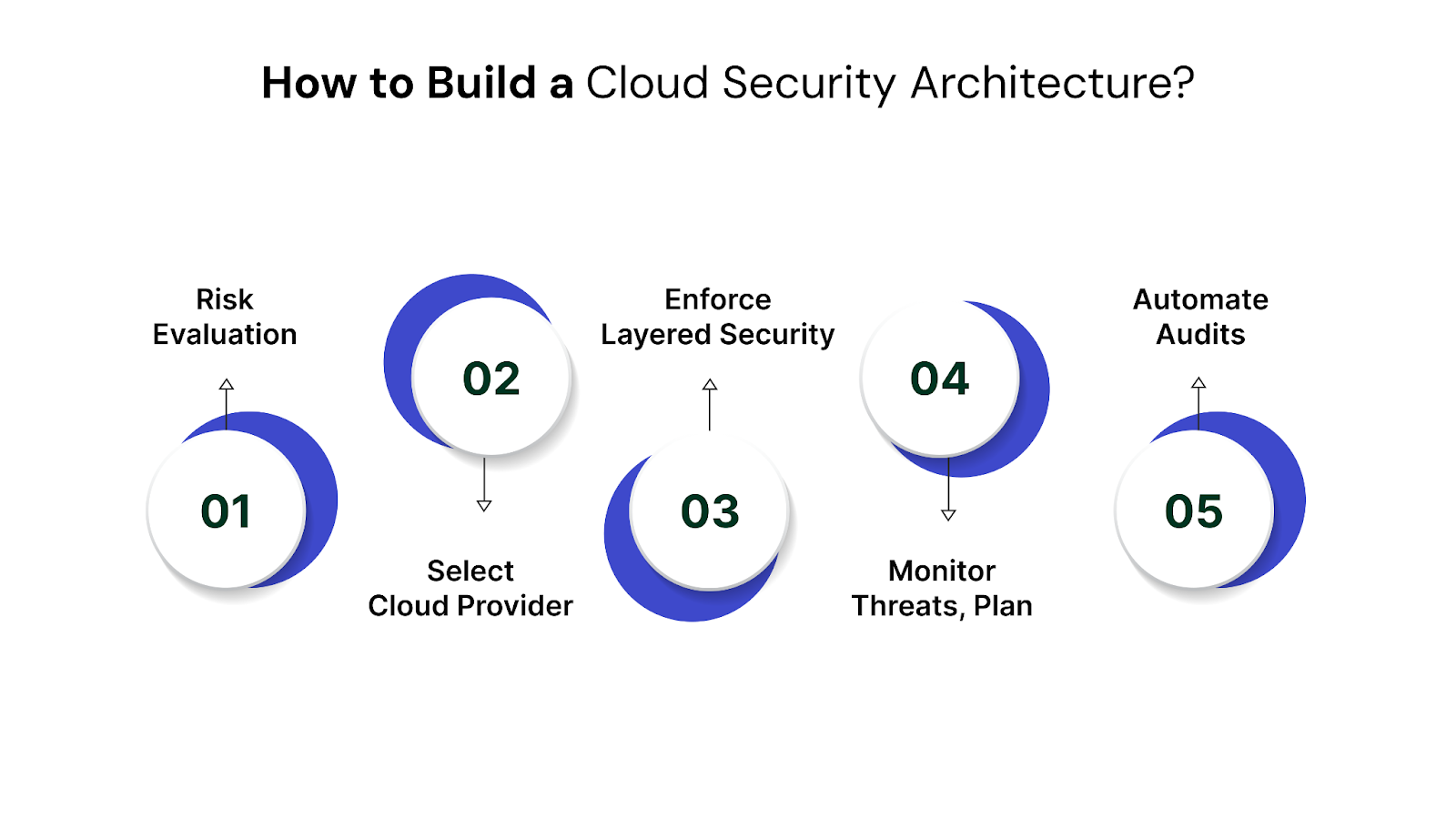
Cloud security is not a one-time setup. It’s a strategic design process that focuses on preventing breaches, securing access, and maintaining visibility across your cloud environment. Every step, from risk assessment to real-time monitoring, plays a role in reducing exposure and keeping systems resilient.
The following framework breaks down how you can build a reliable, multi-layered cloud security architecture that meets both operational and compliance goals.
Step 1: Conduct a Risk Assessment
A risk assessment identifies sensitive data, vulnerable systems, and user behaviors that could expose your environment to threats. This step highlights what needs protection and where weaknesses may already exist.
Some examples include:
Understanding these vulnerabilities early allows your team to plan and implement targeted defenses.
Step 2: Choose a Cloud Provider and Understand the Shared Responsibility Model
Every cloud provider offers a different set of security features and tools. Choosing the right one depends on your workload, team experience, and business priorities.
It is also important to understand who handles which part of the security. The shared responsibility model varies based on the type of service you use:
Step 3: Implement Multi-Layered Security
A layered approach ensures that if one security control fails, others remain in place to reduce risk. Each layer addresses a specific threat category.
Identity and Access Management
Data Encryption
Network Controls
This setup ensures data is secure both in transit and at rest, while also limiting unauthorized access.
Step 4: Monitor Threats and Create an Incident Response Plan
Even with preventive controls in place, threats can still emerge. Real-time monitoring and a response plan are essential for containing damage and restoring services quickly.
Security Monitoring
Incident Response
An effective response plan reduces downtime and helps maintain customer trust.
Step 5: Automate Compliance Checks
Manual audits can miss important risks or become outdated quickly. Automating security checks ensures your environment is always aligned with required standards.
Cloud Security Posture Management (CSPM)
Automation reduces the time and effort required to remain secure while also ensuring continuous monitoring across services.
With the importance of cloud security clear, it’s time to focus on the core principles that guide a secure setup across any platform.
Curious about how cloud services can support your business? Get the full breakdown in our quick guide to cloud computing solutions.
Once you’ve built the foundational structure of your security setup, the next step is to understand how the components work together in practice. That’s where the architecture comes into play.
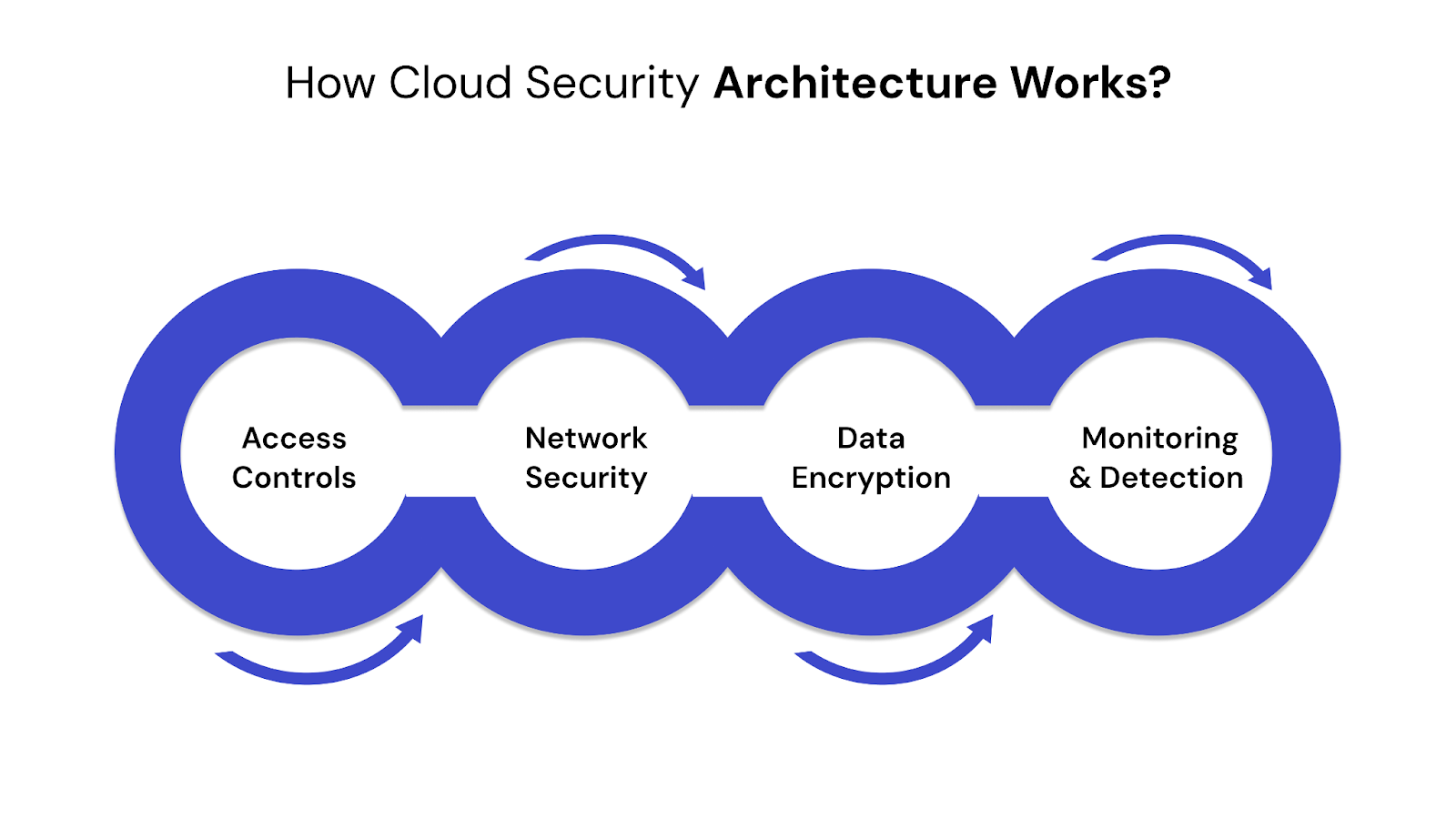
Cloud security architecture relies on multiple interconnected components to safeguard your cloud environment. Each element plays a distinct role in protecting systems, managing access, securing data, and identifying threats.
The following components form the foundation of this architecture:
1. Access Controls
Access controls define who can interact with your cloud resources and under what conditions. These systems authenticate users and assign permissions to limit unauthorized access.
Common tools and practices include:
Access control acts as the first layer of defense, ensuring that only trusted users can reach critical systems and data.
2. Network Security
Network security protects cloud traffic by filtering, monitoring, and verifying all connections to your environment. It prevents unauthorized access and blocks common attacks at the perimeter.
Key practices include:
This layer helps enforce boundaries and control how data flows across cloud services.
3. Data Encryption
Encryption protects sensitive data by making it unreadable to unauthorized users. It ensures that even if data is accessed without permission, it cannot be understood or misused.
Encryption methods are applied at different stages:
Encryption supports privacy and compliance requirements while reducing the risk of data leaks with data migration resources.
4. Monitoring and Detection
Monitoring systems provide real-time visibility into cloud activity. They track events, analyze patterns, and detect potential threats early.
Tools in this layer include:
This layer strengthens your ability to detect intrusions and act before significant damage occurs.
Together, these components form the structure of a secure cloud system. They work in coordination to protect access, monitor usage, secure information, and maintain trust.
Now that you understand how these security layers function together, it’s important to clarify who manages what, especially when working with cloud service providers.
Gartner projects that by 2025, nearly 99% of cloud security failures will be due to customer-side issues. To prevent this, it’s important to understand how responsibility is shared between you and your cloud provider.
Each cloud model has a specific breakdown of responsibilities. This clarity helps prevent common risks like weak access controls or incorrect configurations.
Here’s how the responsibility shifts across service models.
This model gives you control over the computing environment. You manage everything you install or run within it. The provider takes care of the foundational infrastructure.
For example, deploying a Linux instance on Amazon EC2 means you're responsible for patching the OS, configuring firewalls, and securing user access. The provider only ensures the host machine and infrastructure remain available and functional.
PaaS lets your team focus on application development. The provider delivers and maintains the underlying environment, including infrastructure and runtime.
Consider a developer using Azure App Service. If sensitive information is hardcoded into the application or if access keys are left exposed, the resulting risk is your team’s responsibility, even though the platform is managed.
SaaS applications are fully managed by the vendor. While the provider maintains infrastructure and application availability, you are still accountable for how users interact with the system.
For instance, if an employee uses a weak password in tools like Google Workspace or Salesforce, any resulting data breach is attributed to poor user-level security, not the software provider.
FaaS, also known as serverless computing, allows you to deploy individual functions without managing servers or long-running processes. The provider handles the infrastructure, scaling, and runtime. You are still responsible for securing the code and its interactions.
For example, running a function on AWS Lambda removes the need to manage servers. However, if your function includes exposed access tokens or fails to validate inputs from users or third-party services, the risk lies with your team.
As cloud adoption grows, knowing your security responsibilities is essential. But unclear roles can lead to serious risks. Here's what can go wrong if they're overlooked.
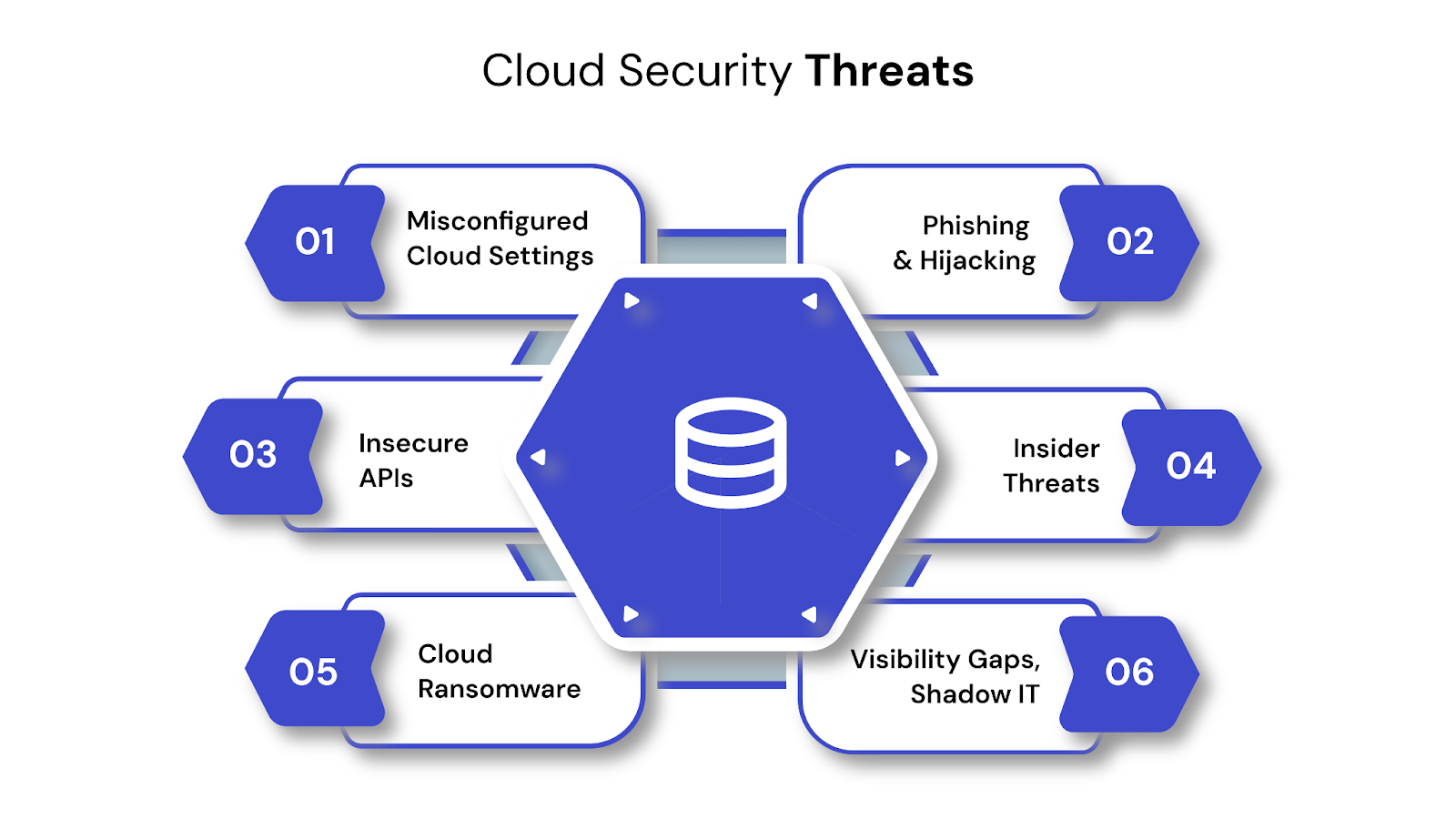
Cloud adoption continues to rise, and so do the risks. Security threats in the cloud are no longer rare or isolated. They now impact organizations of every size, across industries.
In fact, according to IBM’s 2024 X-Force Threat Intelligence Index, cloud environments were targeted in over 34% of all cyberattacks last year, with misconfigurations and compromised credentials being top entry points.
These threats target misconfigurations, identity weaknesses, and software vulnerabilities. The points below outline six of the most frequent and dangerous issues you should plan for.
1. Misconfigured Cloud Settings
Misconfiguration is one of the leading causes of cloud data breaches. This often happens when storage services or compute instances are deployed without secure settings. A publicly accessible storage bucket can expose sensitive data without any direct attack.
Misconfigured environments are typically the result of rushed deployments, missing security reviews, or a lack of visibility.
Example
Several large-scale breaches occurred when S3 buckets were left open to the internet without authentication.
How to reduce the risk
2. Phishing and Account Hijacking
Phishing attacks are common in cloud environments where users access systems through web interfaces. A single stolen password can give attackers control over multiple cloud services, depending on permissions.
These attacks often involve emails or messages that appear to be from internal tools or trusted vendors.
Example
An attacker sends a login link that mimics the organization’s cloud dashboard. Once an employee enters their credentials, the attacker gains full access.
How to reduce the risk
3. Insecure APIs
Cloud platforms rely on APIs for internal and external interactions. If not properly secured, APIs can allow unauthorized access to critical systems and data.
Poor authentication, lack of encryption, or missing input validation often leave these entry points vulnerable.
Example
A public API with no rate limiting and no user validation could be exploited to extract data at scale.
How to reduce the risk
4. Insider Threats
Not all security risks come from outside the organization. Insiders may abuse their access or unknowingly expose data. In many cases, organizations fail to limit internal permissions or monitor data flows effectively.
These threats are difficult to detect because the actions often appear legitimate.
Example
A former employee still has access to cloud files and downloads confidential documents after leaving the company.
How to reduce the risk
5. Ransomware in the Cloud
Ransomware threats have evolved to target cloud platforms. Attackers no longer stop at on-prem systems. They also go after cloud backups, storage services, and SaaS data.
If an organization’s backup strategy relies solely on the cloud, an attack can result in complete data loss or forced payments.
Example
A cloud database is encrypted by malware, leaving the organization without access until a ransom is paid.
How to reduce the risk
6. Lack of Visibility and Shadow IT
As teams adopt multiple cloud services, platforms, and third-party integrations, IT and security teams often lose track of what is being used and how it’s configured. This lack of visibility leads to unmanaged assets, unmonitored data flows, and unknown entry points for attackers.
Shadow IT refers to cloud services used without official approval or oversight. These tools may lack basic security measures or violate compliance policies.
Example
A team stores customer data on an unapproved file-sharing platform without encryption or access controls. This platform gets breached, putting sensitive records at risk.
How to reduce the risk
Before wrapping up, it’s important to look at one final step that often gets missed but plays a crucial role in keeping your cloud secure.
Building a secure cloud environment starts with the right architecture. From access controls and encryption to continuous monitoring and threat response, each layer of your system must be carefully designed to handle evolving risks.
This guide walked you through the key concepts of cloud security architecture, real-world threats, and strategies to strengthen your setup. Whether you're managing customer data or critical applications, security should be integrated from the ground up to support both compliance and resilience.
If your current setup lacks visibility, consistency, or control, QuartileX can support your transition to a more secure and scalable cloud framework. Our solutions are aligned with your environment, not tied to specific vendors.
Cloud Security with QuartileX
At QuartileX, we help businesses secure their cloud environments with structured, security-first architectures built for scale and compliance.
Here’s how we support your cloud security initiatives:
Our focus is on reducing risk without slowing you down. Whether you're launching new services or protecting legacy systems, our team works closely with you to build the right defense.
Ready to reinforce your cloud architecture? Get in touch with QuartileX to build a security model that fits your business.
Cloud environments require security that works across virtual networks and shared resources. Unlike traditional perimeter-based models, cloud security emphasizes identity, workload-level protection, and automation.
Use configuration scanning tools, enforce role-based access controls, and automate audits using CSPM platforms. Regular reviews help avoid gaps in settings that lead to breaches.
Security reviews should be performed after every major deployment and at regular intervals, such as monthly or quarterly, depending on your industry requirements.
Threats include misconfigurations, phishing, insecure APIs, insider access, ransomware, and data exfiltration. Architecture ensures controls are in place to detect and prevent these risks.
Yes. A well-designed architecture supports hybrid and multi-cloud environments by using consistent identity policies, encrypted communication, and shared monitoring layers.
Yes. Zero trust is a key principle in cloud security. It requires verification at every layer and limits access based on context, not just roles or network location.
From cloud to AI — we’ll help build the right roadmap.
Kickstart your journey with intelligent data, AI-driven strategies!